By Marcus Nadenau

FROM SIMPLE TO SOPHISTICATED
Various forms of access control have been available for many years, ranging from simple mechanical systems, or a combination of mechanical, electrical and/ or electronic to the sophisticated solutions we have today. The choice, of course, depended on requirements and budget as it still does. For example, one relatively low-cost solution is a straightforward identification device with numeric or alphanumeric buttons that only requires a user to key in a Personal Identification Number (PIN) for a solenoid-enabled mechanism to open the door. This did not need any human monitoring and was (still is) a reliable and effective method despite its limitations. A similar, even simpler method, is the use of a personal metal or plastic key, the latter similar to that used for hotel room access and an example of programmable access.
Another method is CCTV monitoring that requires human intervention where an operator permits (or denies) access to a person required to identify his- or herself, usually by pressing a buzzer and speaking into a microphone. A step further, and still considered a leading-edge technology, is IC contact cards that have been in use for over 30 years. Since the 1970s, smart card technology has reflected steady advances in chip capabilities and capacity, as well as increases in the number and variety of applications, including banking, personal data archiving and highly secure physical access control. A number of modern access systems employ technologies such as biometrics, mechatronics, RFID and IP.
|
|
|
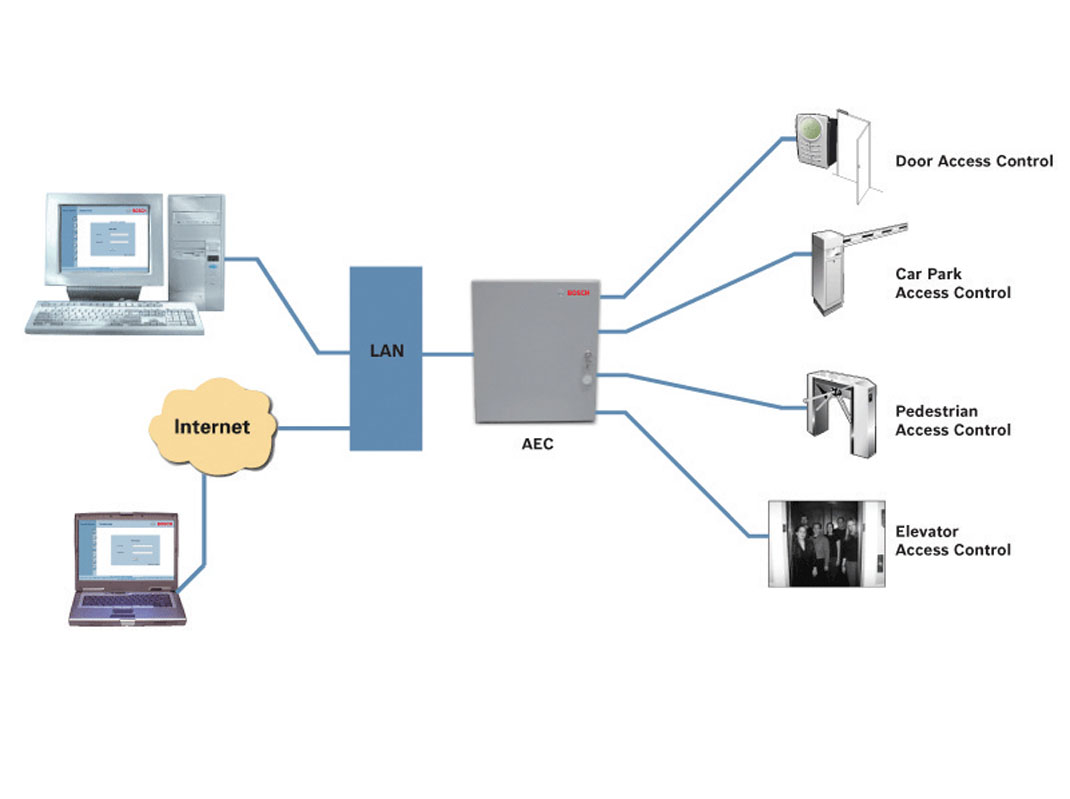
Figure 1. A single Access Easy Controller (AEC) can connect up to 16 card readers. The system reports entry and exit events in real-time, which are archived into a database for immediate person, location and date/ time information.
(Source: Bosch Security Systems) |
ACCESS EASY CONTROL SYSTEM
Introduced at the end of 2005, the Web-based Access Easy Control System (AECS) was developed by Bosch primarily for small- and medium-sized enterprises. It comprises either one Access Easy Controller (AEC) for a single location or up to 20 multi-location AECs with one Access Easy Master Controller (AEMC) that supports a maximum of 320 Wiegand card readers.
The system provides fast and full control of access readers, doors, elevators, gates, sensors, alarms and other security devices. Identity card access control allows definition of when and where access is allowed or disallowed and for whom. The AECS has built-in time attendance tracking for added control of business resources that can greatly reduce audit time and errors caused by manual data entry. Moreover, tracking employee work time adds to management efficiency. Also built-in is intrusion monitoring and alarm. In the event of unauthorized intrusion, the monitoring center immediately issues an email or SMS alert to allow quick reaction to the security breach. Configuration is facilitated through advanced input/output programming for preset applications such as Guard Tour, Feed Through Interlock, Up-Down Counter and Exit Door. Remote networking, administration and maintenance are enabled through a modem connection.
AECS is a ‘network-ready’, ‘plug-and-play’ system that can be easily connected to an existing TCP/IP LAN or WAN via an Ethernet port or switch. Any computer within the network can be used as a client for security monitoring, control and management irrespective of operating system, whether Windows, UNIX, Linux or Mac OS. The system’s built-in Web server uses any program that supports Java, such as Internet Explorer, Netscape Navigator, Mozilla Firefox or Opera. Recent additions to the AECS have extended its functionality and application scope.
Another access control solution developed by Bosch is the Access Personal Edition, an ideal, low-cost entry-level software package for applications that require a high level of security but do not initially need a large-scale, powerful access control system. It is based on the intelligent Access Modular Controller (AMC), the advanced hardware platform used in a number of Bosch security systems that communicates through TCP/IP and RS485. This allows users to easily scale up to the Access Engine (ACE) of Bosch’s Building Integration System (BIS), described further on in this article. Scaling up means that users can benefit from the broad functionality of the ACE without the expense of new access control hardware. Access Personal Edition provides adequate administration of up to 2000 cardholders, 64 readers and 16 clients. Other features include anti-passback that protects against unauthorized use of cards, automatic card cancellation after expiry or temporary use, optional PIN code identification, and day and time modules. Administration is further facilitated through the multi-user module that allows system access from multiple workstations.
A further innovative improvement is the AMC2 4W, the latest version of the Access Modular Controller and ideal for larger installations. Used in the ACE from version 2 onward, the compact AMC2 4W controls a group of one to four access points through ID card readers and fully processes access logic at assigned entrances or exits. Eight analogue inputs allow status checks to be made, while eight relay outputs are used to activate door-opening devices and/ or generate security activation and signaling. The unit stores information in a battery-buffered memory and a compact flash storage element, which ensure that authorization checks can be carried out offline. Up to eight AMC2 4W units can be connected to a host computer through one RS232/RS485 AMC-MUX converter. More recent installations use IP networks, for which the integrated 10/100 Ethernet interface of the AMC2 4W provides fast communication with the ACE without the need for additional devices. The ACE application administers up to 32 serial connections, allowing 32 AMC2 4W units to be connected in series. However, Bosch recommends a maximum of eight AMCs per serial line, up to 200 units. If the number of AMCs is to exceed 200, adding a second PC as concentrator is also recommended. Software is compatible with earlier AMC versions. The unit’s front-mounted display provides immediate information at the controller -- an important benefit for installers.
|
|
|
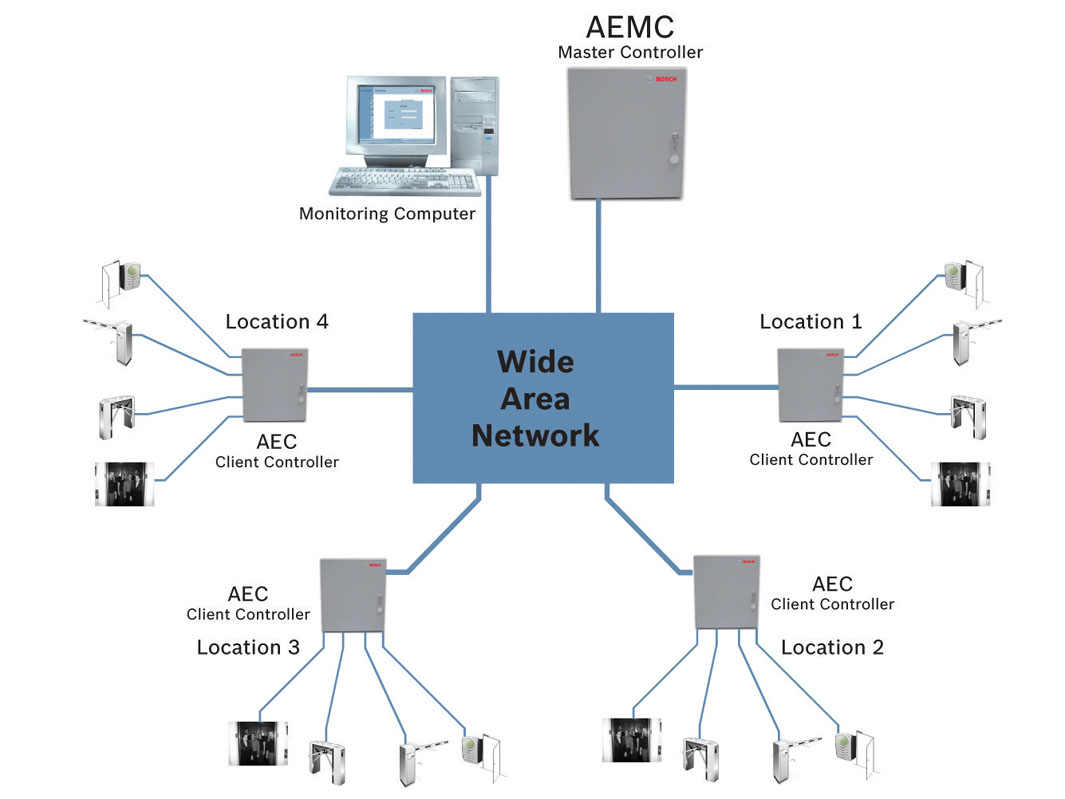
Figure 2. Multiple AECs in multiple locations -- Up to 20 AECs connected to one AEMC that allows a maximum of 20,480 cardholders in 254 access groups (Source: Bosch Security Systems) |
BUILDING INTEGRATION SYSTEM
Bosch adopted a holistic approach when developing the Building Integration System (BIS) by analyzing the overall Facility Management (FM) requirements of business and other offices, manufacturing and warehouse complexes. This took into account the complexity of modern building technology and the many different equipment and system requirements, ranging from temperature control, fire and intrusion detection and alarm systems, public address and emergency evacuation, access control and video surveillance.
Based on OPC (Object Linking and Embedding for Process Control) open systems connectivity, Internet technology and AutoCADTM graphics format, BIS is an optimal addition to existing building automation or FM systems. Being OPC-compliant, BIS supports interfacing with a wide range of standard field buses such as EIB, LON, Profibus and BACnet. Many third-party suppliers around the world already provide OPC servers for these applications. The system relies on floor plans provided by a building’s architect and project engineering office. It is suitable for a wide range of applications including, retail chains, banks, warehouses, university campuses, medical complexes, office buildings and correctional facilities. Interoperability options are available for security, surveillance, building management and process control systems to provide outstanding efficiency, economy and security for one site or many sites managed as one. BIS provides an extremely flexible base on which users can build a security infrastructure step-by-step, starting with one component, to exactly match the organization’s needs and without requiring additional programming.
BIS provides a complete overview of all connected subsystems, panels and the status of individual detectors and alarms, displayed with location maps, action plans, animated icons and audible notification. The client’s organizational structure is optimally modeled to ensure that messages and alarms are properly responded to and acknowledged. Multiple divisions with customized, Web-server-based views for each one can also be easily created. For example, if parts of a building are leased out, tenants can set up their own access control systems and receive their own messages and reports. Existing CAD data can be integrated without having to convert or split diagrams. Subsystem configurations and personnel data from a Human Resource system can be directly imported.
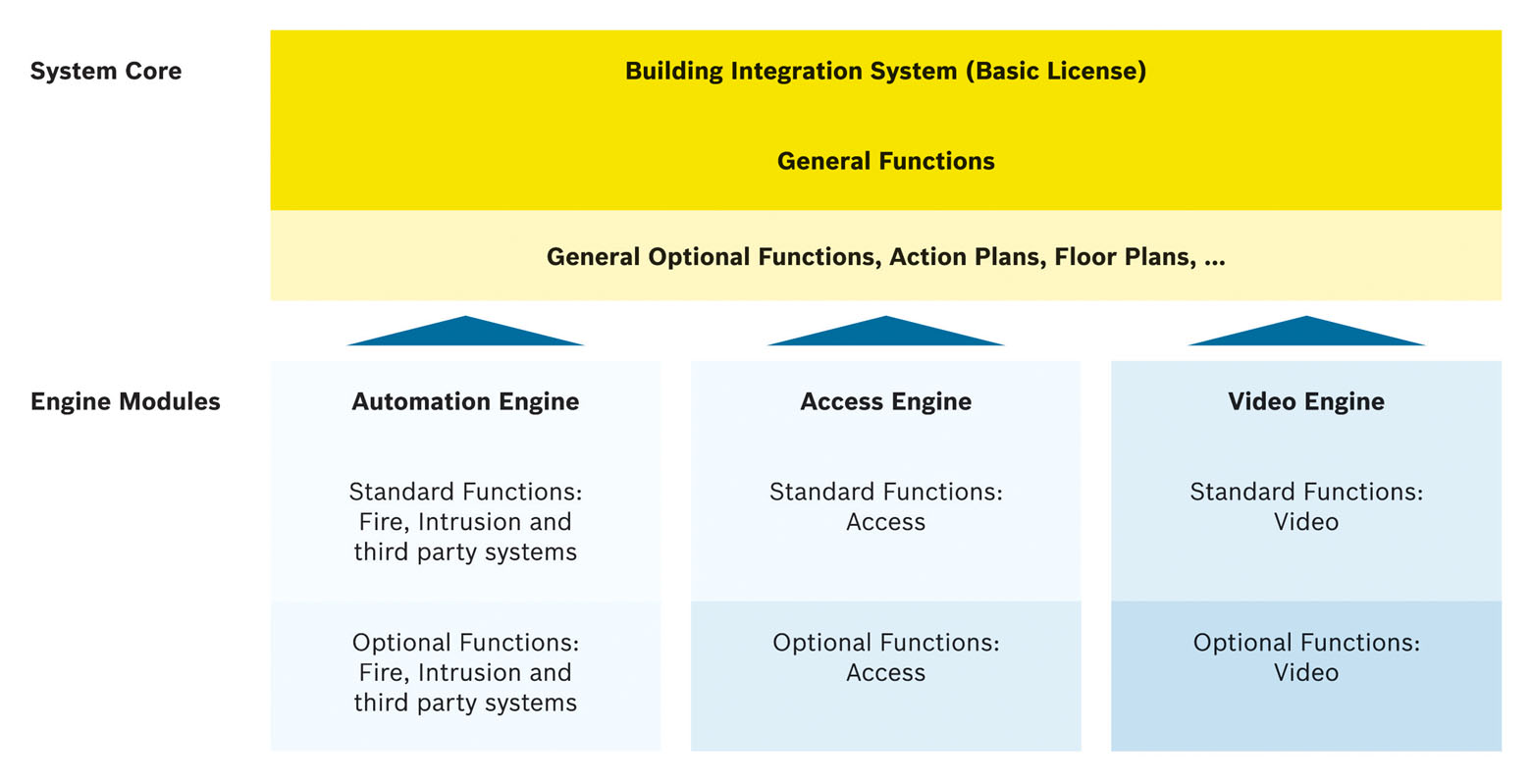
The BIS software platform comprises three engine modules, which can be selected to suit any building configuration and to provide exceptional flexibility through the addition of other modules or software options as requirements expand or change. The BIS user interface is customizable and dynamic, and provides one point of control to manage different systems.
The Automation Engine enables central management of both Bosch and third-party fire and intrusion systems. All property information flows into a single system. Individual building systems are controlled from a single point, and all information is intelligently networked. This makes it easy to monitor a wide variety of subsystems from different manufacturers, including public address, intercom or Heating, Ventilation, Air Conditioning (HVAC) systems. The engine can be freely customized to suit the location’s monitoring and control requirements, thus eliminating the need for time-consuming conversion and recreation of data or redundant data storage.
The Video Engine monitors sensitive areas through CCTV technology and also incorporates both Bosch and third-party video equipment. Various display options provide more possibilities and flexibility for mixing and displaying different video sources on the same screen. A virtual guard tour and additional local archive features provide enhanced security. Viewing live or archived images is simply initiated by clicking on a selected camera icon or selecting from a convenient context-sensitive device menu. An external PTZ keyboard supports simultaneous control of auto dome cameras connected to Bosch’s DiBos8 and Divar DVRs and VideoJet/VIP encoders and decoders. Standard cameras connected to DiBos and Divar can be used for motion detection of intruders.
The Access Engine is used in combination with the AMC (or AMC2 4W) to enable seamless access control with identification, authorization checks and data storage. Access alarms and events within the building can be immediately visualized using the common Building Integration System platform and its sophisticated display features. Existing master data can be easily migrated using a flexible import/ export interface. A wide range of peripheral devices is available, including various card readers and advanced access control devices.
|
|
|
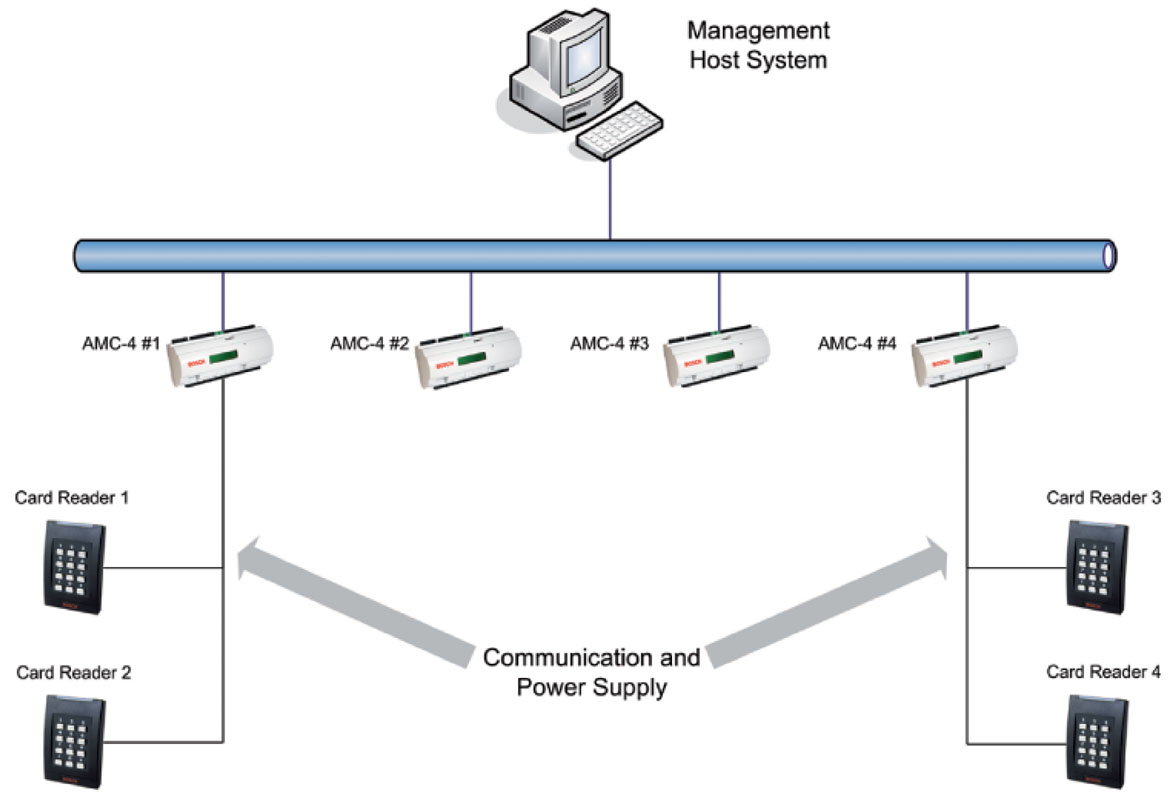
Figure 3. System overview: the AMC2 4W is integrated between the host system (e.g., Access Engine) and peripheral devices. (Source: Bosch Security Systems) |
As businesses, public services, educational facilities and governmental institutions grow, so do the buildings and complexes to contain them and, therefore, their security requirements. Moreover, the increase of theft and vandalism often results in property damage and, sometimes, human injury. The composite ‘bottom-line’ here, is loss of revenue, disruption of services, high cost of replacing equipment and damage repair and probable considerable increase in insurance premiums.
Investment in Bosch’s Access Easy Control System, Access Modular Controller and Building Integration System pays dividends. Integration of security and other building facilities saves time and costs and greatly improves overall operational efficiency. This is achieved through better, centralized control of all functions with faster reaction, simplified maintenance, higher levels of safety and reduction in false alarms and call-out of police or fire services. Today, total integration is being applied anywhere where multiple facilities in multiple buildings or locations need to be co-ordinated, monitored and controlled.
|
|
|
Figure 4. The modular structure of Bosch’s Building Integration System (Source: Bosch Security Systems) |
Marcus Nadenau is Vice President of Business Unit Integrated System, Bosch Sicherheitssysteme GmbH (www.boschsecuritysystems.com).
For more information, please send your e-mails to swm@infothe.com.
ⓒ2007 www.SecurityWorldMag.com. All rights reserved.
|



