By Steve Unger
|
|
|
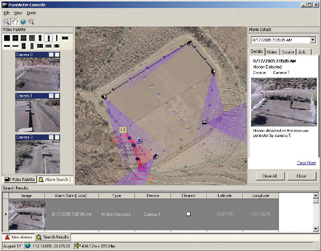
Security console displays video alarms and cameras, enabling users to click and operate multiple cameras. The lower screen displays a history of the alarm and the right screen presents the most current view, used for both live and recorded video. (Photo by PureTech Systems Inc.)
|
It seems as though every day, we’ree reminded of the need for better security systems and devices. The whole scope of our industry is changing.
After generations of dealing with ordinary thieves and vandals, security managers now have to worry about such threats as radical terrorists, suicide bombers, school shootings, infant abductions and psychotic vengeful employees. Contemporary society also requires protection from new varieties of non-violent security risks, such as corporate espionage, identity theft and intellectual-property crimes.
The good news is that while the dangers have increased, so has the ability to deter them.
“It’s amazing how much new security technology is being developed,” says Keith Canova of Tech Electronics, a St. Louis, Missouri-based provider of commercial and industrial security systems. “We’ve been in this business a long time, and we’ve never seen such a range of effective new applications for access control, intrusion detection, personal safety, you name it. And as new technology comes along, we’re also seeing increased interest in all of it.”
Given today’s greater needs for protection, many security professionals are carefully evaluating the latest new products; however, they are often being asked to expand or upgrade their security capabilities without a corresponding increase in budget.
“That’s one of the biggest challenges we’re facing right now, is that security managers are expected to do a lot more with a lot less,” says Larry Bowe, president of PureTech Systems. “They’re faced with tremendous problems to solve, often with no additional funding. As a result, they’re really looking for systems that can help automate things they’re now doing manually, or to help them be more effective with fewer people.”
Leading-edge manufacturers are well aware of this dilemma, and they are aggressively developing new ways to make traditional security programs more efficient and cost-effective.
INTEGRATING SYSTEMS
“Much of the innovation behind security technology today involves getting the various components and peripherals to work together more efficiently,” Canova explains. Many new software interfaces, digital applications and wireless products help to make seamless integration of systems readily achievable.
As a case in point, Closed-Circuit Television (CCTV) has been around a relatively long time, but recent advances can now make a CCTV system do much more than it ever could before. By integrating and automating support functions within a security network, a system’s video monitoring can be set to activate only upon detecting motion in a certain area, such as the presence of a human form in a distant part of the facility.
Bowe’s company, PureTech, offers such technology. One of their products, the PureActivTM system, is an automated outdoor surveillance solution especially designed to detect security breaches at perimeters and remote environments of wide-area facilities, such as airports, seaports, fuel-storage depots, reservoirs, utilities and other locations with critical infrastructure.
The system actually uses geographic mapping technology to locate and position security devices, cameras and alarms on a map on the point-and-click user interface display. That provides a ‘real-world’ perspective of the entire site under surveillance. By associating latitude and longitude coordinates with every object it detects and each alarm it controls, the system is instantly able to produce map displays indicating the location of any event.
“Let’s take the scenario of a fence integration,” explains Bowe. “When our system gets an alarm, it knows exactly -- within a few feet -- of where the triggering event occurred. It would then steer a camera right to that location and validate what was happening. If there really was a perpetrator, the system will pick him up and the camera would actually start tracking him automatically. Or, once notified of the event, security personnel can use their controls to maneuver multiple pan-tilt-zoom cameras simultaneously at the remote location. That enables them to accurately assess the situation in progress by spatially associating video and alarm data, all from the control panel.”
Such advanced, integrated intrusion-detection solutions may even be programmed to initiate several more security responses. When cameras are triggered, the system can automatically lock gates and doors in the area, turn on lights, shut off valves, transmit audible announcements, page guards on patrol and so on. Better yet, the alarm can activate digital video recording, which will tag and earmark the event in real time, and archive the data as evidence for future investigations.
DETECT, ANALYZE, RESPOND
“This new technology really takes things to a higher level for us,” said Steve Grosvenor, a security systems integrator with Millennium 3 Technologies (M3T) based out of Phoenix, Ariz. “With a more proactive, intelligent alarm system that’s tied to real events in real time, a facility’s security personnel will be able to get involved much sooner. It’s a lot more effective than having guards staring at 16 video screens, and being expected to recognize a threat with their eyes. Now the system will alert them to any real event.”
To optimize their own counter-measure procedures, security managers can establish specific rules and schedules within an advanced detection system. The system can be programmed to make phone calls or send e-mails with response and acknowledgement instructions, transmit signals to a remote central monitoring facility or even send video images to a PDA.
Event-generated detection systems also make it much easier and more economical to store recorded images. Even if security cameras are always on, they can be running at a slower speed to facilitate image compression and storage. But then when triggered by motion-detection, the cameras bump the recording up to a higher frame rate to capture more of the event and promote investigative accuracy.
MAKING IT POSSIBLE
Increased security threats and demands are obviously tremendous motivators for system developers and manufacturers, but many of the latest innovations owe their existence to recent advances in technology.
“Just four or five years ago, it would have been considered very early in these new trends,” says Bowe. “Now we have the analytics, the video image processing capabilities and so on. We’re able to take more complex algorithms and move those into affordability.”
Changes in Internet technology and transmission capabilities have also been advantageous for the security industry, as has the trend from the analog world to digital cameras, IP enabled cameras and the many types of data reduction.
The various new technologies available to system integrators also create unprecedented flexibility and scalability. It’s easy to expand or modify a security network as needs change. The PureActiv system, for instance, was designed so that one server could handle up to 200 remote sites, each with eight cameras, all distributed across numerous geographically separated facilities. If more than 1,600 cameras are ever needed, it simply calls for a second server.
“What’s really enabled these developments, to a large extent, is the processing power that’s available on the platforms,” Bowe adds. “W hat maybe you had to do with a Cray computer some years ago, you can now do on a simple PC or a Digital Signal Processor box.”
Other high-tech systems help to minimize the problem of nuisance alarms. Passive-infrared motion detectors activate only upon sensing a temperature change in a specific area, such as an intruder’s body heat, measured in contrast to a background. Many of today’s sophisticated motion sensors feature “immunity,” which means they can effectively differentiate human shapes from small animals. Certain detection devices include a sensitivity adjustment, so they can be set to filter out non-threatening vibrations from wind, thunder or passing vehicles. A good example of this is how PureTech’s PureActiv system turns standard security cameras into smart sensing devices. “With some very straight forward set-up and calibration, our system is able to detect particular objects and behaviors such as a truck traveling in the wrong direction or a person approaching a fence. We’re able to accomplish this with standard CCTV cameras. The PureActiv software contains the intelligence to enable this more precise detection,” says Bowe.
A SAFER FUTURE
Some of the new tools almost seem like science fiction, such as the wireless technology that’s becoming more common in security. Now it’s possible for mobile sentries or patrols to carry a wearable, hand-held scanner/server, which is wirelessly linked to their system’s database. That means if a guard at a remote location encounters someone on the premises, he can perform an ID check by actually taking a live video shot of the person in question and transmitting that image to the company’s electronic files for immediate verification.
New wireless technology also makes it possible to transmit real-time video images from a vehicle that needs security, such as an armored car, school bus, or public-transit systems.
Another futuristic security process is “biometrics” -- the growing use of unique physical features as a way to verify identification. Typically a biometrics-based system reads a person’s fingerprint of hand geometry, but other applications may include scanning the iris of the eye or voice-recognition.
“As complex and wide-reaching as some of the new technology may appear, these systems aren’t designed just for big corporations or sprawling facilities,” adds Tech Electronics’ Canova. “All companies need good security, and with the new scaleable, modular types of products, anybody can afford a highly effective intrusion detection or monitoring system.”
Ours can be a dangerous and scary world, and there’s no denying that reliable security is vitally important. Fortunately for all of us, it just keeps getting better.
“Obviously, the top objective is to protect lives, assets and critical infrastructure,” says Bowe. “And if we can help someone improve the effectiveness of their surveillance with less staff or without additional resources, it’s even better.”
Steve Unger is a writer with Canyon Communications.
For more information, please send your e-mails to swm@infothe.com.
ⓒ2007 www.SecurityWorldMag.com. All rights reserved.
|



