This article looks to avoid the usual technological rhetoric approach and provide end users with a list of performance-based requirements that will leave the responsibility of providing the correct solution with the system provider. All too often we are inundated with technical specifications, background information and conflicting argument over what technology to adopt. The industry experts tender for this work and leave the responsibility back with the end-user who effectively accepts a list of ¡®kit¡¯ not a solution that is designed or programmed to meet the needs of the original requirement. We can be more objective and performance oriented. What we need to understand is what happens at ground level where we finally manage the resulting systems.
By Ian Fowler
MEETING THE RISKS OF TODAY
In order to develop a suitable security system for your organisation, it is essential to first build a strategy. Defining your core business processes is the first step, and allows you to then identify essential resources and facilities that need protection. From here, you must consider any threats to these resources and focus on those you consider most likely to occur. Even if the chance of threat is small, the short and long-term impact on the business may be large.
A TYPICAL TRADING BUSINESS PROCESS
The following diagram attempts to identify some of the critical elements involved in keeping a company afloat. This includes resources, whether material or personnel based, and buildings or the facilities within them.
Core Business Processes
Although the core elements of businesses may differ, they all have a number of processes in common. It is important at this stage to determine what the priorities are. In general, they tend to be a mixture of the following points:
Critical Elements Involved in Keeping a Company Afloat
|
.jpg)
|
|
Figure 1. Critical elements involved in keeping a company afloat (Source: Norbain) |
Client/market Accessibility
Our channel to our target market must always be available in order to maintain the business order stream. A client will always expect to be able to make contact with a supplier within a short time frame. Short amounts of incoming message downtime can mean our clients start to become concerned about our trading ability.
Staff
How do they access the site? If the site has multiple entrances, each of these needs to be correctly secured. Do staff have to leave any personal belongings for a period of time whilst occupied doing other things? For example, meetings, dealing with visitors or whilst at lunch. The staff need to feel they can trust the location, the environment they work in and their colleagues. Just as importantly, access points needs to be suited to employee needs, e.g., wheelchair access.
What measures are required to ensure our staff feel valued, cared for and safe? This is dependent on the environment and type of work being carried out. For example, staff at a football stadium have very different safety requirements to those at a distribution warehouse.
How is staff morale? Are there any known issues with staff dissatisfaction that need to be taken into consideration?
Process, Equipment, Plant or Machinery
These factors become a concern when they are singularities, that is, there is no back up if something is damaged, stolen or fails to work.
Property
If your property is damaged to the extent that you can¡¯t carry out business, there are obviously severe cost implications. Although it is possible to ¡±hot site¡± and move to another location, the time and expense involved are often prohibitive.
Stock
What sort of stock does the company carry? Finished electrical goods with a good street value are more vulnerable to shrinkage than low cost, unfinished parts.
Local Services and Infrastructure
We don¡¯t have a great amount of control over these factors, so a standby plan is the best chance you have to prevent severe disruption to your business should an incident occur.
Transport, Telecommunications, Water, Gas, Electric
The consequences of these services being disrupted is obviously great, so security to prevent their disruption and the disruption of any backup power is essential to any business strategy.
SINGULARITIES AND PRESSURE POINTS
A simple chart can be used to help you determine sensitivity and singularity. Once they¡¯ree identified procedures can be put into place to help protect or offset risks to these elements. These items could also be ranked to allow you to prioritise potential risk.
Determining Sensitivity & Singularity
.jpg)
Figure 2. Cost breakdown of I-AM Trading Ltd. (Source: Norbain)
Putting Values to Risks
If we look at a fictitious company, I-AM Trading Ltd., we can see how to put values to risks.
Here¡¯s the scenario:
-
I-AM Trading Ltd is a ¡Ì1m pa business
-
It has 300 loyal and satisfied clients
-
It has conscientious staff and sales
-
It buys from 50 suppliers
-
It is a leading edge company in its field
-
Raw material costs vary, but some are very high
-
It has a specialist core team
With known annual costs of ¡Ì600k, we then need to qualify where these costs are going:
Cost Breakdown of I-AM Trading Ltd.
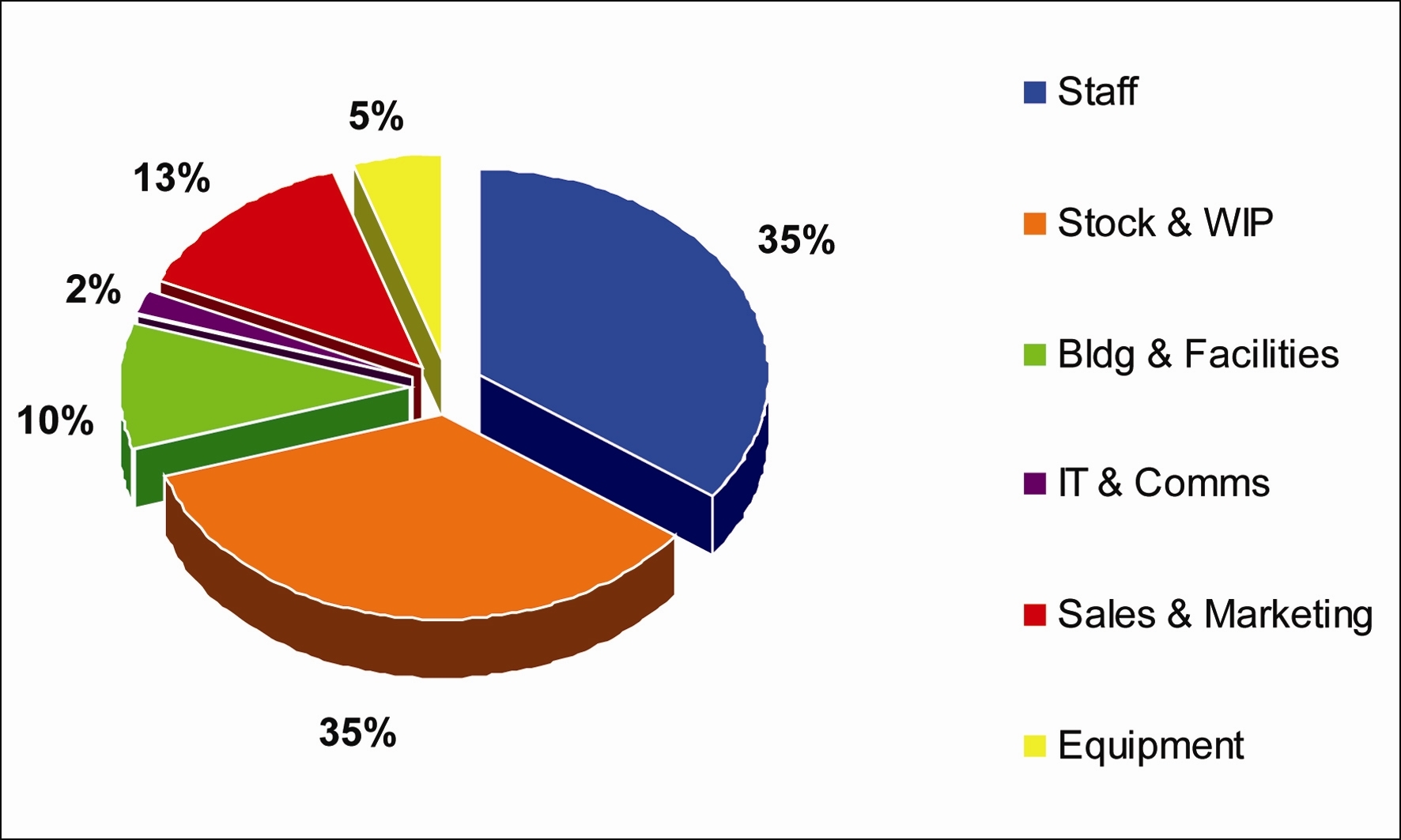
Figure 2. Cost breakdown of I-AM Trading Ltd. (Source: Norbain)
From here, you can define how operating cost equates to exposures to potential risk.
-
The loss of a given facility, process or person can stop the whole business.
-
The stoppage and reduction in billing values is a real way to assess business continuity losses.
-
The recovery cost and lost time should, therefore, be determined for each risk point.
-
Combining recovery costs and lost billing costs we can start to see the values we risk losing.
-
A major impact of output loss is that if you cannot supply your client base, your clients will have to seek an alternative supply. Namely your competitors.
So, in the event of an incident, the cost of recovery, lost days and market share damage for a ¡Ì1million turnover company such as I-AM Trading Ltd. may well be:
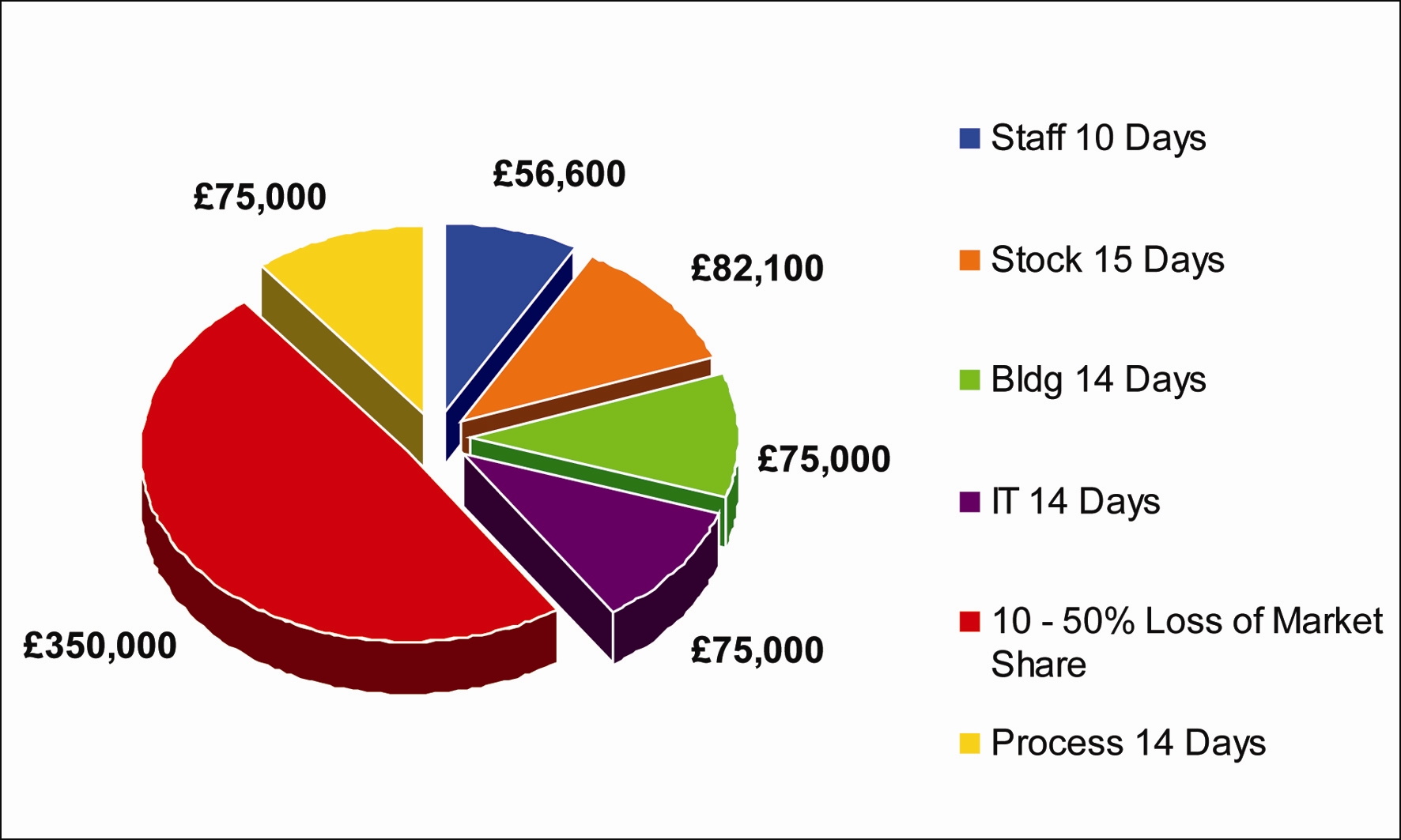
Figure 3. The cost of recovery, lost days and market share damage for a ¡Ì1million turnover company such as I-AM Trading Ltd. (Source: Norbain)
Total value of risk ¡Ì638,000
CAN YOU INSURE AGAINST THE LOSS?
Yes, you can offset the cost of the risk, but you need to be prepared to answer insurer¡¯s questions on what measures you¡¯ll be taking to reduce the risk. To do this, you need to understand how to work with the odds and understand where threats to your business come from.
For example:
Once you¡¯re considered all these points, you can cross check the potential threats to your list of business risks and analyse the probabilities. In general, it¡¯s realistic to use ratios of 300,000:1 per threat. Combining probabilities may reduce the odds to nearer 100:1 or 500:1 for any element.
SIZING THE BUDGET
We¡¯re already determined that I-AM Trading Ltd, a ¡Ì1m turnover company, carries a risk of ¡Ì638,000. Good business sense says offset the most obvious possibilities.
If we use odds of a very conservative 200:1, we can set our business continuity and security budget at ¡Ì3,190pa (200th of ¡Ì638,000).
OTHER BENEFITS OF IMPROVED SECURITY
A well thought out security system doesn¡¯t just need to be there for insurance purposes. It can also benefit the business and the way in which we manage clients and staff. For example, in a retail outlet, CCTV doesn¡¯t need to be restricted to keeping watch for any theft. It can also be used to see how customers use the store, what times are the busiest, how they move around the aisles, how long they browse for and so on. This can give you an invaluable insight into your customer and their needs.
Staff also benefit from improved security as it can offer them better personal safety.
In banks, clever use of physical and electronic security, such as access control, dramatically reduce any risk they may face from the public.
Of course, CCTV footage can also be used to record any incidents that may occur and be passed to the police to aid the recovery of goods and bring the perpetrators to justice.
A BUDGET OF ¡Ì3,190 PA
So, if I-AM Trading Ltd. put aside an annual budget of ¡Ì3,190, they could take up a leasing deal capable of installing access control and CCTV systems before taking into account other issues such as loss reduction. The question now is what Key Performance Indicators (KPIs) should be set in order to obtain the maximum benefit for the budget.
DRAFTING KPIS FOR ACCESS CONTROL
The first step is to define all the groups requiring access to the site and for each group determine what the issues are:
Valid Time Zones for Access
Different areas of the business have differing working hours that need to be taken into consideration. Access to the offices by maintenance or IT is often 24/7. However, in a city-based business, more socially active staff under the influence of alcohol, may attempt to access the site late if it is valid to do so, bringing unnecessary risks with them. Clearly not all staff will need access during the same hours.
Work Places and Access Routes
This examines the physical locations and their associated risks. Zones may need to be established, each with relevant user types set up for them and cohesive access routes.
Critical Locations or Access Points
These can be areas of great value, or areas that are deemed to be hazardous. Examples include IT rooms, cash handling, research or bio-hazard laboratories and hazardous material stores.
Card Issues per Month
Staff, contractors and visitors will all require cards, tokens or enrolment to gain access to the various areas of the building. You need to consider the skill requirements of setting up and administering such a system, along with the cost and effort of administering it on a daily basis.
Once this has been decided, you need to consider who will manage the system and whether to use a central or point of use administration system.
Drilling down a little further, there are a number of further points to consider:
-
Ease of use for daily traffic
-
Ease of use for disabled or staff carrying loads
-
Anti pass back or challenge strangers
-
Ensure that the lock and door can handle the amount of traffic expected and that they are robust enough for the usage levels.
-
Administration of changes - how easy is this, who would handle it
-
Type and price of keys, fobs and tokens
-
The fire officer needs to accept the system as safe.
The ability to integrate access control into the CCTV system is, for many, a powerful option that allows for tighter control and the tracking of personnel around the site.
DRAFTING KPIS FOR CCTV
As with access control, there are a number of key performance indicators that need to be identified:
Purpose of the Observation
Intervention -- what will you use to initiate a response by the police? This generally tends to be an alarm trigger, or a real-time observation by personnel or security staff. Archiving for detection and prosecution -- the system will simply observe the incident so that staff or police can determine what leads there are.
Define Time Frame for Incident Notification
This is relevant in terms of minutes, hours or days and is directly related to the recording capacity of the DVR. Alarms may need to be tied to events, especially if a fast response is required.
Establish Critical Locations
This is related to both internal and external locations. Once established, you need to control access to them, or monitor them.
Establish Traffic Habits and Cycles
Target the most popular routes and ensure that all bottlenecks and shortcuts have been identified.
Identify Clear Management Responsibility
It is essential to clearly apportion responsibility for the management of the whole system. This prevents confusion, which could lead to important information being overlooked. A single point of contact that will ¡®champion¡¯ the system is the most effective method of control.
Identify How and Where Evidence Will Be Secured
There are three main options here:
1. At point of capture - when image size is too great to transmit in real-time
2. At local hard disc recorders and then networked
3. At the security office - all information needs to reach that point in real-time
Again, drilling down we can examine the KPIs for an actual CCTV system:
-
It is critical that images are clear and fit to meet the purpose.
-
All wide views must have an associated close up view.
-
For management or administration of staff, it is important to know who was doing what, and when they were doing it.
-
For legal, criminal justice or health and safety purposes, identification views need to be less than 1.3m along the vertical edge measured where the main target would be standing.
-
When looking to export images, the following points are key:
-Removable media CD, DVD, Smart Media
-Printable still shots - meeting the subject¡¯s access rights (an important part of the data
protection act)
THE IMPORTANCE OF POSITIONING
Once you¡¯re followed all the criteria for specifying your CCTV system, it¡¯s essential that it is correctly set up to give you the best chance of collecting clear, sharp and usable images. A Rotakin¨Ï can be used to this affect.
A Rotakin¨Ï is a standard test target, 160cm tall by 40cm wide. It can be measured as a proportion or percentage of the vertical view captured by the camera when the Rotakin¨Ï is placed at the targeted position, or at the extreme distance for a given performance expectation.
The four main performance levels are:
1. Identification - large enough to identify a stranger
2. Recognition - less critical than identification as the target may be known to us
3. Detection - where an observer alerted to a presence should be able to determine the target is in the scene with minimum searching
4. Monitor and Control - this type of view lends itself more to event management looking for anomalous behaviour within crowds of people, such as at a stadium football match
|

|

|
|
Camera badly positioned showing rotokin¨Ï
(Photo by Norbain) |
Camera badly positioned showing example subject (Photo by Norbain) |
|

|

|
|
Camera well positioned showing rotokin¨Ï
(Photo by Norbain) |
Camera well positioned showing example subject (Photo by Norbain) |
DON¡¯T REDUCE YOUR CHANCES
It¡¯s important to crop your image as closely as possible to your target area. Wider views give us smaller targets and, therefore, poorer identification and leads.
Another point to consider is when to capture the image. This is often done on point of entry to a building, for example, into the reception area. However, there are two important points to consider here: 1) Because of the light coming in through the doors, it¡¯s often difficult to actually see details of each person; 2) By simply entering the building, the person hasn¡¯t committed any crime. A more suitable position for the camera would be to record people as they leave the building. This way, you can see if they are carrying any goods and the lighting is far more balanced, so details are clearer. To further improve your chances of identification, you need to aim for at least three pictures per second whilst they¡¯re in view.
IMAGE BENCHMARKS
To quantify the image quality you receive from your CCTV system, you need to ask for detailed sample images from the supplier or manufacturer. This image should represent the minimum acceptable quality of a recorded image (not a live image). You can then compare the final recorded image with the sample -- they should be identical in quality. The following images would represent high through to minimal compression. However, all of these would still be presented through a high-resolution output circuit in the order of DVD, D1 or 4CIF. As you can see, there is a dramatic difference in picture clarity.
TARGET CONTENT
The images show how a shot has been set up in a particular location. Here we can see:
These shots add value to observation or context views of >20%R.
If you intend to secure your generic business risks, you need to aim to get the best value for money by making the system provide security that fits in with the way your business works. This way you can be assured that, should an incident occur, either during work hours, or when the business is secured for the night, you can identify ¡°Who Did It.¡±
Ian Fowler is now a Security Consultant with Buro Happold Limited, but wrote this Article while employed as a Technical Training Manager of Norbain.
For more information, please send your e-mails to swm@infothe.com.
¨Ï2007 www.SecurityWorldMag.com. All rights reserved.
|



