Accurate and fast identification of individuals is the key to the future of physical and software security systems. IDS Worldwide has the key.
By Bill Scott
|
|
|
Photo by IDS Worldwide, Inc. |
Historically security systems were designed to allow access using “hardware” (e.g. a key or unintelligent devices such as a password or ID card) which can be passed around, lost, or stolen and provide immediate uncontrolled and unmonitored access to ANYONE who has them in their possession because it was the “hardware” and NOT the individual that controlled access. Terrorist, criminals, and even employees have proven themselves easily capable of bypassing traditional “password only” or card-based security Systems.
LEARN FROM THE PAST
The first mass market fingerprint scanners were introduced in the 1990s, and used surface-sensing technology to basically take a picture of the surface fingerprint pattern. A variety of methods were developed to convert these patterns into electrical signals, including infrared gauging, mechanical force measurement, electrical capacitance, and temperature measurements. Although these methods worked under controlled indoor settings, they were unable to capture useful fingerprint images under real-world operating conditions. They often could not capture usable images from people with skin that was dry, thickly callused, or worn smooth by mechanical or chemical means. The failure of these devices to work properly for significant percentages of the user population hindered the widespread adoption of biometric identification.
TRUEPRINT TECHNOLOGY
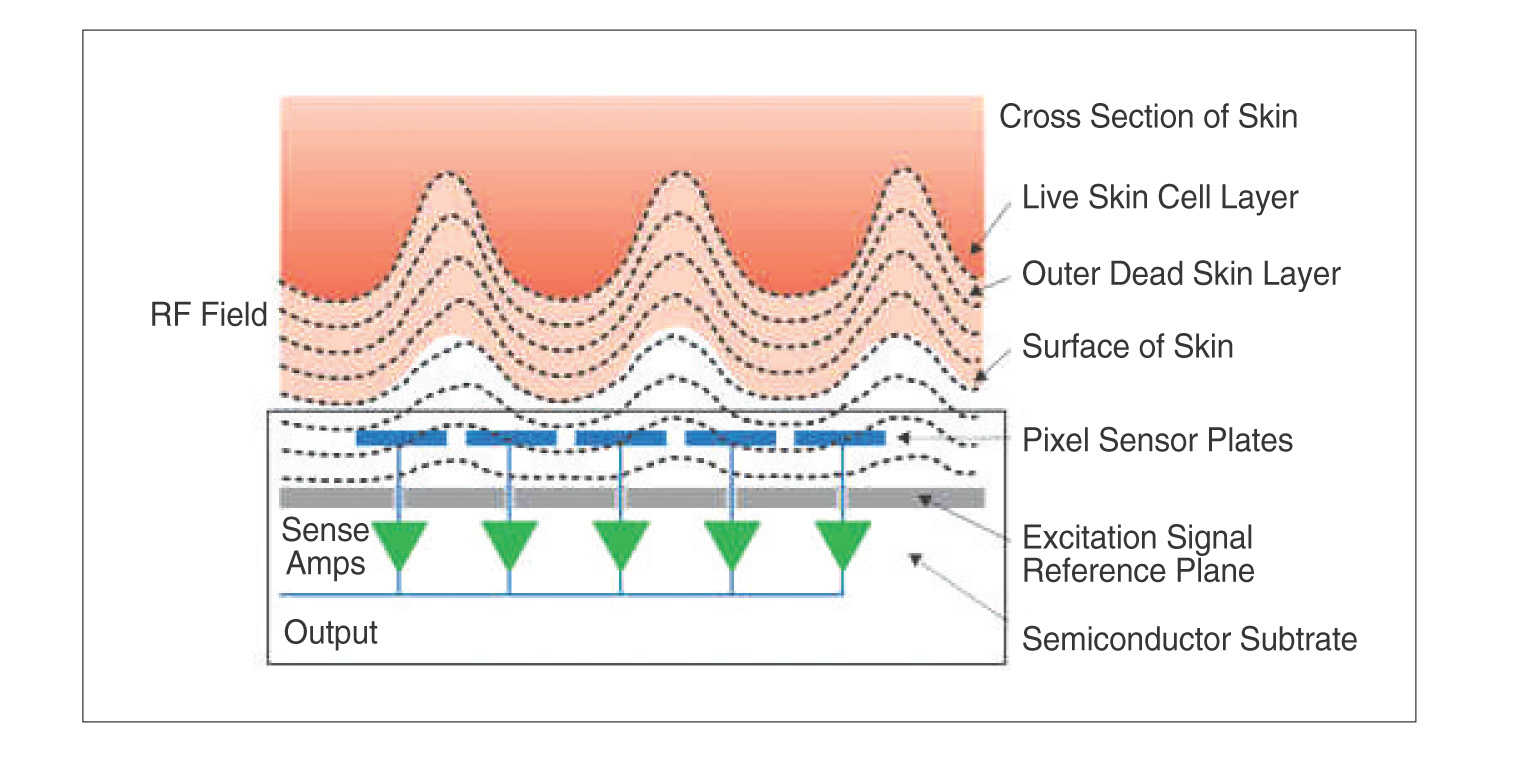
TruePrintTM technology was developed by AuthenTec, Inc. to overcome these problems, and allow reliable operation in real world environments. It is a unique semiconductor-based fingerprint reader technology, that uses small RF signals to detect the fingerprint ridge and valley pattern. The RF electronic imaging mechanism works by reading the fingerprint pattern from the live, highly-conductive layer of skin that lies just beneath the skin’s dry outer surface layer. TruePrintTM-based sensors are less affected by common skin surface conditions -- including dry, worn, calloused, dirty or oily skin -- that can impair the ability of other sensors to acquire accurate fingerprint images.
|
|
|
Figure 1. TruePrintTM is a Trademark of AuthenTec, Inc., a manufacturer of the world- leading chip technology used in Bio-Guard 384-Bit Security and Bio-Encrypt Software Systems Biometric Security Systems. (Source: IDS Worldwide, Inc.) |
IDS BIOMETRIC SECURITY SYSTEM
IDS utilizes TruePrintTM technology in its biometric-based hardware and software security systems, transferring an electronic print into an encoded file, along with any other information desired by the user (e.g. name, SS #, address, employee ID #, criminal history, levels of clearance, picture of individual, etc). This file can be stored inside basic locks or access control hardware for on the spot ID and access control; or in various levels of specialized software that can be modified to meet ANY user application and economically implemented at all levels, from the home, through corporate and enterprise levels, through government & military, through nationwide security applications.
The heart of the IDS system is the AES4000 sensor, which is packaged in a JEDEC-standard 144-pin LQFP (Low-profile Quad Flat Package). The AES4000 sensor is comprised of a sensor matrix, a drive ring, and supporting electronics. The purpose of these elements is to reliably detect the presence of a finger placed on the surface of the sensor matrix, and to produce a digital image of the fingerprint.
-
RS232 Port controller is available at the output, to connect the hardware to the host system.
-
RS485 is available to connect more than one device (Door Scanners) present at some vicinity.
-
10 Base-T Ethernet is for networking
When a thumb is placed on a finger print sensor, the sensor output comes in the form of bytes. The total number of bytes may be adjusted between 1152-4608 bytes by using the configuration registered of the sensor chip. These bytes are received by the microcontroller unit either by using fast serial interface or parallel interface. This data of the fingerprint sensor is saved in the SRAM and then sent to either RS232 port or RS485 or 10 Base-T Ethernet according to the requirement at the suitable Bode rate. These bytes are converted into a signature using Fast Fourier Transform Technique in the host computer. The signature will be matched with those entered into the employee security & information module in the host computer or main authentication server. If the signature is authenticated, respective output action will be taken (e.g. door opening, attendance time marking, HR management, security access, etc.)
IDS combines TruePrintTM technology, with its own hardware and specialized software, to provide reliable, cost effective, biometric-based physical and software security systems such as Bio-Track.
There are Six Major Sub-System Components in the IDS Bio-GuardTM Software Systems Biometric Security System:
-
IDS BioEncrypt-384TM: 384 Bit, 18 Level Encryption Software
-
Employee Security & Information Module
-
Biometric Security Fingerprint Scanning Technology
-
Biometric Physical Security Access Devices
-
Biometric Activated Data Access
-
SMART-Scan Fingerprint Search/ ID/Authorization
1. IDS BioEncrypt-384TM Security Software: It is important that both the data stored on computers (servers, desk tops, lap tops) is encrypted, using a very high level algorithm, to prevent ANYONE from gaining physical access to your sensitive data. The level of threat increases dramatically when Internet connections and emails are taken into account. The BioEncrypt-384TM Software system is installed ON computers, and prevents the opening of Windows, without the proper Encryption Code. IDS combines Biometric Security readers on IDS Biometric USB Flash Drives, Mouse’s, and Keyboards to first identify the Individual, then provide this Encryption Code to enable the computer to turn on and operate. Once operational, all data and online transactions are fully encrypted using the company’s patent pending BioEncrypt-384TM Bit, 18 Level Encryption Algorithm.
2. The Software System starts with this Information Module, which MUST contain every pertinent detail of Authorized Individuals. These should include:
-
Employee ID, Social Security, Drivers License Numbers
-
Contact Details, Department, Job and Grade Settings
-
Current Picture of Employee, and ALL Fingerprints
-
Known Criminal Record
-
Security Clearances (Gov’t), Company Security Level of Access
-
Specific Physical and Data System Access Areas
3. IDS Biometric Fingerprint Scanning Technology reads the “Electronic Fingerprint” that exists beneath the skin on everybody’s fingers. This Electronic Fingerprint remains, even if the skin has been damaged (by accident or on purpose). It is impossible to “fool” even using such well know “spy” techniques as fake fingerprint “films” or other more grisly movie methods.
4. Biometric Enabled Physical Security and Access Devices
-
Door Locks
-
Access Control Devices (Door, Gate, Perimeter)
-
Computer Access Control Devices (FLASH Stick, Mouse, Keyboards)
-
Credit Cards and Access ID Cards to prevent fraud and theft
5. Biometric Enabled & Encrypted Computer and Internet Access Components
-
Computer and System Access Control Software
-
Online Access Control to protect Access to Systems over the Internet
-
Encrypted Software System for Online Banking and Purchases, to prevent ID Theft and Fraud
6. SMART-Scan System Software
Theory of Operation
When the system is powered up, it will ask for a username and an authentication signature before startup. The user puts his thumb or finger on the finger chip sensor. The sensor will convert the finger print image into bytes (generally from 1152 - 4608 bytes). These bytes will be stored in the NV RAM temporarily, then will be sent to the host computer; and an “encrypted signature file” will be formed. These signatures will be matched against those stored in the Individual Security & History Module, and a determination made if that individual is authorized access to that device or computer or system. If NOT authorized, Windows will NOT start, and access will be denied, and in either case a report will be generated. BOTH the Fingerprint and User Password can be combined for additional security. The system can be configured to require reset of fingerprint authorization, at user definable time frames.
Software Configuration
The SMART-Scan Authentication System requires that only Authorized Administrators can add new Individuals. Again, every Admin action is documented and a report made. A new user will be required to enter their Fingerprint impression twice, and set up their password, to be entered into the data base.
After that whenever a user logs into the system, the system will demand an authentication and will check all accounts for the authentication. After successful authentication, the SMART-Scan system will allow the user to use the computer, or gain access to authorized areas.
Biometric Fingerprint Scanners can be interfaced with Door Locks, Access Control devices, Keypad or Mouse, to require that users are fully authenticated and authorized to gain access. Examples of typical Biometric Security Applications include:
-
Interfaced with Airline Baggage & Tickets, to prevent switching of tickets, theft of baggage, checking bags and not getting on the plane, etc.
-
Biometric Print entered on Credit and ATM cards to prevent fraud
-
Biometric Print Checks to prevent fraud
-
Biometric Print Driver Licenses to ensure ID
-
Biometric devices to restrict access to computers, systems, files, data
-
ONLINE Biometric devices to prevent online fraud
-
Home or Business Biometric Door Locks, interfaced with Security Systems
The SMART-Scan system offers a relatively low upfront cost to implement., Biometric Chips and Fingerprints on Credit Cards, Driver Licenses, Checks, Mouse add only a few cents to the cost in quantity.
For further information on the Bio-Guard 384-BitTM Security Systems system, and other IDS Biometric Security products, go to www.ids-worldwide.com.
Bill Scott is VP of Business Development, IDS Worldwide, Inc. (www.ids-worldwide.com ).
For more information, please send your e-mails to swm@infothe.com.
ⓒ2007 www.SecurityWorldMag.com. All rights reserved.
|


