The security of wireless voice services and mobile data are key considerations for users and their employers. Based upon the results of a recent In-Stat survey, a majority of users overestimates the risk, misunderstands the security threats that do exist, and looks for protection from sources that cannot help.
The Problem
The current reality is that cellular voice and data services based upon digital technology are as secure as wireline networks. The bigger problem is that end-users lose, or have stolen, a large number of mobile devices. Extrapolating from the survey, In-Stat projects that over 8 million devices in the U.S. will go missing this year alone. Furthermore, smartphone users, the ones with the most access to sensitive information, are 40% more likely to lose a device.
If we look at the projected value of lost mobile devices, we see that smartphones represent a disproportionate value of lost hardware. This does not include the value of data that could be accessed should an organization not know about the loss of the device.
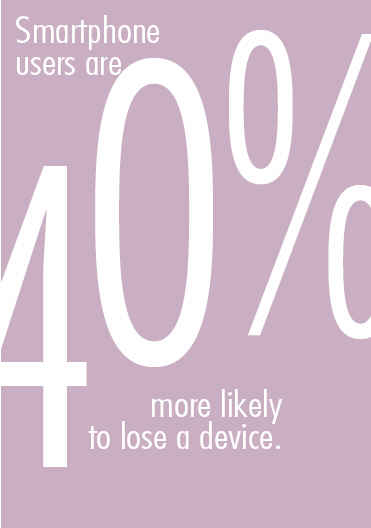 Taking over Control Taking over Control
Since it is impractical to “put the genie back in the bottle” and limit access to corporate information to landline connections, organizations need to take over at least some control of these devices. Too many organizations allow end-users to select their own devices, mobile data networks, and degree of access to corporate databases.
The problem with this is that users select the method that is most convenient and costs less, not necessarily the one that is most secure. Based upon this survey, users are extremely misinformed about security threats. Most are concerned with problems that have been solved for almost a decade.
Getting in Front of Mobile Security
Compounding the security problem is that users reject even minimal steps to increase security. For example, many users resent that a carrier can disable a stolen device and many carriers find that many use default passwords, an obvious security risk. The first step for organizations to get in front of mobile security is to assume corporate liability for mobile communications. As long as corporate users pursue individual liability as an acceptable option for business use, it seems inevitable that security breaches will become more common.
For more information, please send your e-mails to swm@infothe.com.
ⓒ2007 www.SecurityWorldMag.com. All rights reserved.
|



