By Katharina Geutebruck

THE FUTURE IS….
Analog or digital? It’s a pity so much time and effort is invested in answering a question which is based on a false assumption! The two systems are NOT mutually exclusive and each has its own strengths, so it makes sense to use both! Then you can exploit the advantages of both technologies and the resulting hybrid systems offer powerful, practical solutions which are open to future developments and well placed to meet future challenges.
Then why is the market so polarized? Well, many young start-up firms which recognized the potential of digital technology for CCTV, are dedicated exclusively to developing digital solutions. Whereas many older, experienced firms came late to digital technology and offer predominantly analog solution routes.
THE FUTURE OF ANALOG CCTV CAMERAS
In 2004 ninety percent of all CCTV cameras installed in security systems around the world were still analog-based, i.e. with a CVBS- or NTSC-standard analog output. Their greatest advantage lies in their complete compatibility with almost all other devices in the market, whether essentially analog or digital.
In recent years new developments have improved analog picture quality: increased light sensitivity of CCD sensors; better backlight compensation and dynamic range; as well as sharpness and color correction when switching between color and infrared light. Functions such as privacy zones, motion detection and remote setup have been also been refined and are now more affordable. Sensors and cameras are smaller and more powerful. The range is now vast: from budget models right up to real high end ones, and including some extremely high resolution cameras which were previously only used for industrial applications, but are now used with picture analysis. The increased volumes and competition have resulted in enormous price reductions.
I expect other improvements are still to come:
-Day/Night Switching Performance: Optimization of the switch-over point and improvement of picture properties in both modes. Currently there are still focusing problems at the switchover from color to b/w mode, especially with infrared illumination. I anticipate new lenses to avoid the color distortions in mixed light operation.
-Backlight Compensation: CMOS sensors already offer significantly higher dynamic ranges than CCDs but their light sensitivity, color behavior, etc. is still poorer. I expect that both technologies will develop further, with dynamic range of the CCD and the other CMOS sensor parameters being improved.
-Light Sensitivity and Resolution: There is certainly still development potential here, within the limits of the CCIR standard.
-Motion Detection: There will be further refinements in motion detection in cameras.
-Camera Noise from CCD Sensor Warming: Particularly at high operating temperatures when the CCD sensor heats up, it produces more noise and hence poorer picture quality. In future special cameras with CCD cooling will produce less noise and allow higher operating temperatures.
-System Integration: There will be an expansion of direct control of camera functions from the control center as a standard.
NETWORK CAMERAS: TODAY AND TOMORROW
CCTV market specialists all predict that in the long term, new installations will exclusively use network- or IP-cameras -- only the time scale is questionable. Though growing fast, their market share is still small. Network cameras certainly offer great flexibility at installation and in use, provided the network infrastructure is there, but their main handicap is lack of compatibility with each other and with standard control center software and hardware components.
Most network cameras don’t yet match the functionality of the bulk of analog cameras, particularly in relation to light sensitivity, picture rates and flexibility of focal lengths and angles. However, a few do perform better, offering both higher resolution (megapixel-chips) and additional functions such as audio, built-in motion detection, picture storage as well as webserver functionality. But at current low volumes they are more expensive than high quality analog cameras.
Since most network cameras use CMOS sensors they are likely to improve with the performance of the sensors.
A common argument in favor of network cameras runs: ‘Using existing data networks for the CCTV system avoids the need for dedicated cabling.’ But, on many sites the existing bandwidths are barely adequate for data-processing applications, and many IT-administrators will not permit video data on company networks because of large data streams and high demands on bandwidth. In which case dedicated, parallel video networks may be the chosen solution. But even here, system designers soon reach the limits of conventional network technology. With current standard cables only carrying data on a 100Mb network for up to 100m, installations with lots of outdoor cameras need extra active components or a different transmission medium such as optical fiber.
Another challenge for the traditional CCTV market is finding suitably skilled installers who are well versed in IT networks as well as CCTV project engineering. As yet these installers are relatively rare, but the increased popularity of networked picture recording and transmission in recent years has stimulated some improvement. Meanwhile some IT service providers have been taking over the role of specialist security installers.
|
|
|
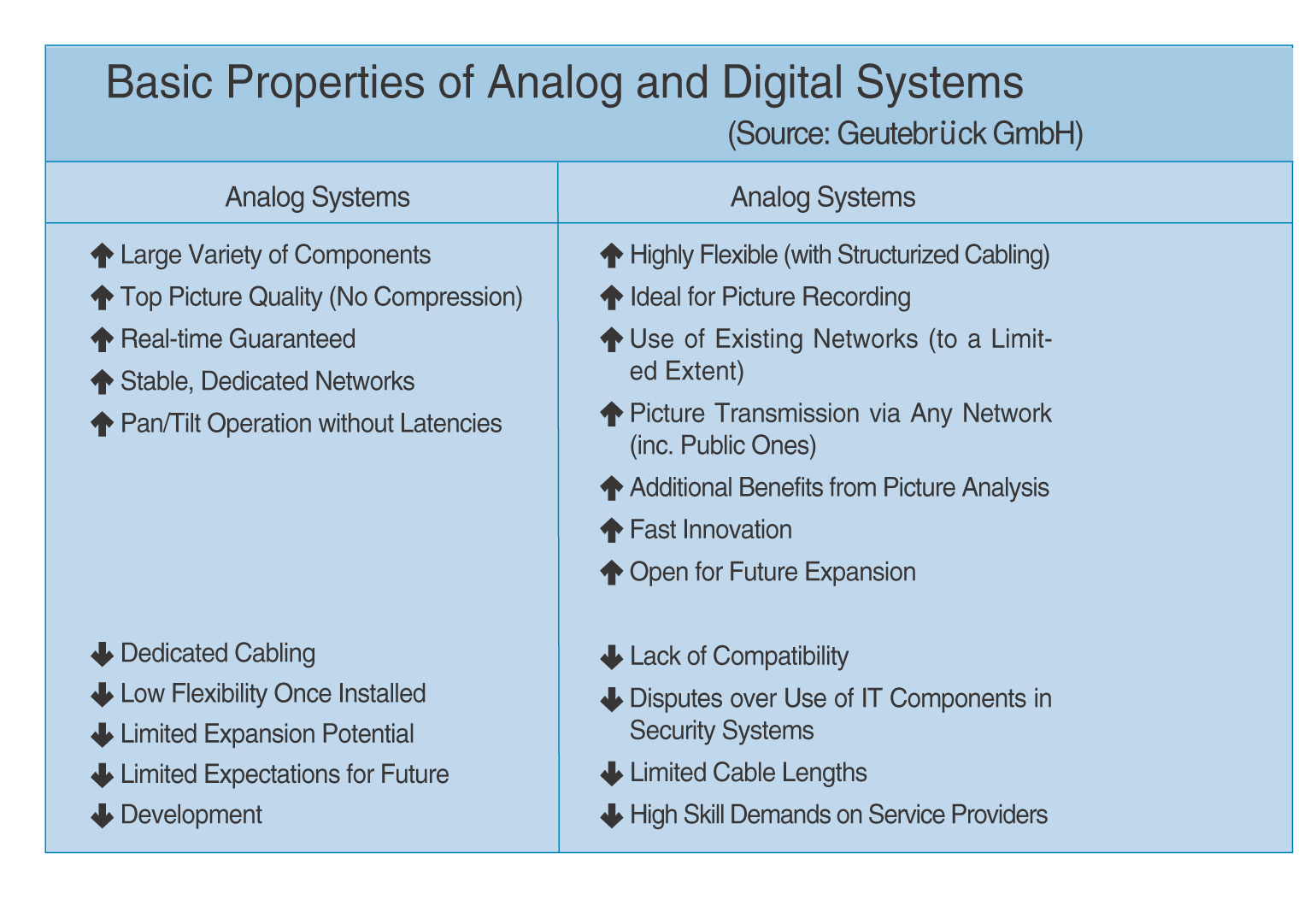
Intelligent picture analysis has advanced beyond test installations, but still leaves much room for development. The above is an example of facial recognition. (Photo by Geutebruck GmbH)
|
NEW TECHNOLOGIES
New technologies from other industries have been significant in the development of CCTV systems in the past, for instance, the CCD sensor, PCs, IT networks and digital picture processing. So what might be next?
In a market which values stability, reliability and continuity, innovations need to be proven before they are adopted, but there are some developments in other areas which seem to offer potential:
-Network Bandwidths in General: 1GBit network products are now used for the so-called backbone, connecting the most important active network distributors. 10GBit transmission products are also available for use with special DarkFiber cabling. This technology requires all the norm guidelines to be followed exactly to achieve full bandwidth availability.
-Broadband Wireless Networks (UMTS, GPRS): While the consumer electronics field dreams of transmitting moving pictures to the laptop or mobile phone, ideally straight from the internet at DVD quality, mobile phone operators are looking for ways to recoup the cost of UMTS licenses. And it is conceivable that UMTS offers potential for CCTV applications. Particularly in large conurbations, temporary installations for large events or for building site protection, could well use UMTS for transmission to a central control room. This connection might be continuous or event-driven. And in the mobile surveillance field UMTS might be used for visual checks on situations in busses or trains.
-Wireless Networks: WirelessLAN, Bluetooth and similar systems offer comparable potential for local areas. Though limited in range, these could provide better information to guards in large building complexes, for example by transmitting pictures to the guard? PDA.
As yet there is little experience in protecting the data in wireless transmission media against unauthorized access and intentional or unintentional external influences. Given the pressures on bandwidth automatic bandwidth limitation functions will be important in digital transmission systems.
For quick decision-making the CCTV operator needs streams of live pictures from every camera viewing an event, with adequate picture quality to see and assess the full action. For later analysis he needs the most detailed pictures possible, but not necessarily such a high picture rate. To fulfill these different requirements, systems need to deliver live video streams independently of the quality and speed of the picture recording.
-Internet: Using secure, encrypted connections (e.g. via VPN-Virtual Private Network) the Internet offers economic (picture) data transfer to any recipient and a means of monitoring remote buildings or transmitting alarm pictures.
-Storage Media: Establishing the cause of an event promptly and efficiently depends on the retention of comprehensive documentation, perhaps for long periods. The user needs redundancy (e.g. RAID-Level), high picture quality, picture rates and long archives -- because they are do-able and affordable. However, these requirements are not easy for the manufacturer and installer to meet because of the sheer volume of recorded data which has to be available and searchable. The future will see the introduction of intelligent storage strategies with backup media for long-term redundancy from IT server systems.
|
|
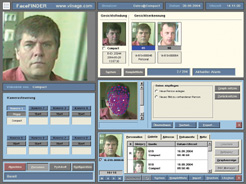
With all algorithms compromises will always have to be made, but the error rates will be improved to make the systems workable for the particular application and situation. The above is an example of number plate recognition for barrier control. (Photo by GeutebrUck GmbH) |
|
.jpg)
|
Ergonomically designed and customized for the operator, the user interface has to be operated intuitively. (Photo by GeutebrUck GmbH) |
PICTURE ANALYSIS
Intelligent picture analysis is probably the biggest driver of growth in the CCTV market. Although already used in lots of new applications, these processes are still young. Character recognition, traffic monitoring and analysis, smoke detection in road tunnels, non-motion detection for identifying unattended objects, and biometric processes such as facial recognition, have advanced beyond test installations, but still leave much room for development.
There is a yawning gap between the user’s expectations and the real performance of these systems. Above all the hardware requirements are often problematic. Many algorithms require enormous processing power and a single video stream will take the full power of a Pentium4 computer and more.
And, as with the now familiar outdoor VMD systems, these newer recognition algorithms involve functionality compromises. The higher the correct recognition rate -- for a critical event, a wanted person, etc., the higher the rate of false positives, where a harmless event is reported as critical, an innocent person is identified as a suspect, etc. And vice versa.
With all algorithms there is an inevitable compromise between recognition rate and robustness, against unwanted alarm reports. In an ideal world different algorithms and recognition systems would be linked to produce the best possible results. However, this will be some time in coming because, as already mentioned, the required hardware resources often lie above the practical and affordable limits. Linking different systems, and running algorithms in parallel, would multiply costs.
So compromises will always have to be made, but the error rates will be improved to make the systems workable for the particular application and situation.
For example, a system which has to recognize authorized number plates and automatically open a barrier, might be adjusted by ‘rounding up’ any inaccuracies in the recognition in favor of authorization. So if a number plate has a total of 8 characters, then some variation in one character is allowed for the decision to be given as ‘authorized.’ The critical level of ‘rounding’ is governed by user settings and depends on what is a workable solution for the situation.
There is generally a great deal of uncertainty, amongst installers and users in the market, because there are relatively few installations in full operation. As yet the specialists needed for the design, engineering, installation and commissioning of such systems are still in short supply.
This technology is also somewhat disadvantaged by the fact that most systems are produced by companies who began life as research establishments or university offshoots. Though highly qualified in their field, they often have little experience in mainstream CCTV. This situation presents a challenge to system houses, to integrate the specialized algorithms into workable security systems to meet the practical needs of the user.
Besides these I also expect other concrete developments in the fields of:
-Behavior Analysis: Critical situations can be recognized by analyzing human movement and comparing it with expected norms for the location. For example: several people appearing in a bank foyer, standing close to each other and then making fast, violent movements, would trigger an alarm picture to the security center.
-Object Recognition and Tracking: Only objects which move atypically -- too fast, too slow, in the wrong direction, etc, and fit specified parameters for size, shape and pattern, are categorized as critical and trigger alarms. This technology is already used in traffic monitoring for detecting wrong-way drivers and jams.
-Data Protection: For example, automatic encryption of faces in a recorded scene, so that each face can be decoded and revealed separately, depending on which person is under suspicion.
CCTV IN OPERATION: EASE OF USE
Technology offers more and more possibilities. The latest video recorder or mobile phone has more options than most users ever master, but a security system like that would be a serious security risk.
On one hand, financial pressure can lead to poorly paid and badly trained operators -- a situation which is hardly conducive to the efficient functioning of the system. And on the other, customers continue to demand more functionality, not just to protect against risks, but to realize additional economic benefits. So given these conflicting pressures, one important trend which will continue is for systems which ease the operator’s burden as much as possible. This is done in two ways:
-Automatic Handling of Routine Tasks: As far as possible routine and preliminary decisions should be made automatically by the system, using intelligent picture analysis and links with various other subsystems through an intelligent management system. This records and switches relevant pictures to the operator with important or critical picture areas marked and useful additional information provided. For example, the garage doorman no longer checks user authorization, the barrier control system and automatic number plate recognition does that. The automatic detection system recognizes congestion or a wrong-way driver and instantly presents pictures to supervisors in the traffic management center. The guard in the emergency call center presses a button to switch a picture of a monitored building to his desktop and checks the intruder alarm using recorded pictures before dispatching a colleague. Ideally, all irrespective of the brand of CCTV system on site!
-Intuitive Operation: Ergonomically designed and customized for the operator, the user interface has to be operated intuitively. Ideally there are graphical site plans of the monitored site, with instantly recognizable symbols and self-explanatory operating processes. In critical situations the system should support the user with brief guidance in simple (local) language. Systems need to withstand accidental or intentional misuse and should have automatic plausibility checks to prevent this.
Incompatibility between equipment from different manufacturers can still be an inhibiting factor. Police and guarding firms in Germany have been calling for the development of a standard picture receiver which will provide a remedy in the near future. International committees are working on unified standards but the issue of standardized component interfaces has been left to the industry itself. In Germany and some other countries for example, there is a strong lobby for the use of the OPC protocol, a communication standard borrowed from automation technology and used for controlling sub-systems through higher level security management systems.
Predicting the future may not be an accurate science, but I’m sure I’m not alone in seeing the potential of the developments I’ve described. So I think it is highly probable that those ideas which aren’t in the GEUTEBRU‥CK development pipeline are already in someone else’s.
Katharina Geutebruck is MD of Geutebrck GmbH. (www.geutebrueck.de)
For more information, please send your e-mails to swm@infothe.com.
ⓒ2007 www.SecurityWorldMag.com. All rights reserved.
|



